[Solved]29 Task 9 Capability Leaking Follow Principle Least Privilege Set Uid Programs Often Perma Q37157317
SEEDLabs–EnvironmentVariableand Set-UIDProgramLab

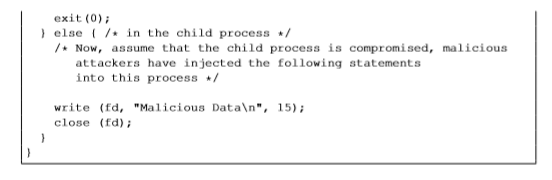
2.9 Task 9: Capability Leaking To follow the Principle of Least Privilege, Set-UID programs often permanently relinquish their root privileges if such privileges are not needed anymore. Moreover, sometimes, the program needs to hand over its control to the user; in this case, root privileges must be revoked. The setuid) system call can be used to revoke the privileges. According to the manual, “setuid) sets the effective user ID of the calling process. If the effective UID of the caller is root, the real UID and saved set-user-ID are also set”. Therefore, if a Set-UID program with effective UID 0 calls setuid (n), the process will become a normal process, with all its UIDs being set to n. When revoking the privilege, one of the common mistakes is capability leaking. The process may have gained some privileged capabilities when it was still privileged; when the privileged is downgraded, if the program does not clean up those capabilities, they may still be accessible by the non-privileged process. In other words, although the effective user ID of the process becomes non-privileged, the process is still privileged because it possesses privileged capabilities. Compile the following program, change its owner to root, and make it a Set-UID program. Run the program as a normal user, and describe what you have observed. Will the file /etc/zzz be modified? Please explain your observation. #include #include #include <stdio.h> <stdlib.h> <fcntl.h> void main () ( int fd; /Assume that /etc/zzz is an important system file, * and it is owned by root with permission 0644 * Before running this program, you should creat the file /etc/zzz first. fdopen (“/etc/zzz”, O RDWRI O APPEND) if (d-1) printf(“Cannot open /etc/zzzn) exit (0); /Simulate the tasks conducted by the program/ sleep (1) /After the task, the root privileges are no longer needed, it’s time to relinquish the root privileges permanently setuid (getuidO getuid returns the real uid/ if (fork) /In the parent process close (fd): exit (0) else/in the child process /Now, assume that the child process is compromised, malicious attackers have injected the following statements into this process write (fd, “Malicious Datan”, 15) close (fd) Show transcribed image text 2.9 Task 9: Capability Leaking To follow the Principle of Least Privilege, Set-UID programs often permanently relinquish their root privileges if such privileges are not needed anymore. Moreover, sometimes, the program needs to hand over its control to the user; in this case, root privileges must be revoked. The setuid) system call can be used to revoke the privileges. According to the manual, “setuid) sets the effective user ID of the calling process. If the effective UID of the caller is root, the real UID and saved set-user-ID are also set”. Therefore, if a Set-UID program with effective UID 0 calls setuid (n), the process will become a normal process, with all its UIDs being set to n. When revoking the privilege, one of the common mistakes is capability leaking. The process may have gained some privileged capabilities when it was still privileged; when the privileged is downgraded, if the program does not clean up those capabilities, they may still be accessible by the non-privileged process. In other words, although the effective user ID of the process becomes non-privileged, the process is still privileged because it possesses privileged capabilities. Compile the following program, change its owner to root, and make it a Set-UID program. Run the program as a normal user, and describe what you have observed. Will the file /etc/zzz be modified? Please explain your observation. #include #include #include void main () ( int fd; /Assume that /etc/zzz is an important system file, * and it is owned by root with permission 0644 * Before running this program, you should creat the file /etc/zzz first. fdopen (“/etc/zzz”, O RDWRI O APPEND) if (d-1) printf(“Cannot open /etc/zzzn) exit (0); /Simulate the tasks conducted by the program/ sleep (1) /After the task, the root privileges are no longer needed, it’s time to relinquish the root privileges permanently setuid (getuidO getuid returns the real uid/ if (fork) /In the parent process close (fd):
exit (0) else/in the child process /Now, assume that the child process is compromised, malicious attackers have injected the following statements into this process write (fd, “Malicious Datan”, 15) close (fd)
Expert Answer
Answer to 2.9 Task 9: Capability Leaking To follow the Principle of Least Privilege, Set-UID programs often permanently relinquish… . . .
OR

